Graduate Essay Writers
Only the most qualified writers are selected to be a part of our research and editorial team, with each possessing specialized knowledge in specific subjects and a background in academic writing.
To hire a writer, fill the order form with details from your nursing assessment task brief.
Posted: March 9th, 2022
Study Bay Coursework Assignment Writing Help
Case articulation
Staysure.co.uk Ltd specialises in insurance coverage and monetary companies within the UK and Europe. It was shaped in 2004 to offer journey insurance coverage and expanded additional to offer residence, motor, well being and life insurance coverage together with some insurance coverage merchandise. In October 2013 Staysure.co.uk confronted a safety breach whereby over 100,00 dwell bank card particulars together with different private particulars of the shoppers have been compromised. This safety breach affected 7% of the shoppers who had bought insurance coverage from Staysure earlier than Could 2012.
Earlier than Could 2012 the agency saved the cardboard numbers of the shoppers together with the CVV numbers and different private particulars like buyer title and addresses. The cardboard particulars have been encrypted however the CVV numbers have been fed as plain textual content into the database though the cardboard safety particulars mustn’t have been saved in any respect in line with the business guidelines. The chief government of the corporate mentioned that these particulars have been saved within the system to Help clients of their renewal course of. After Could 2012 the corporate ceased storing these particulars. The server on which the web site server was based mostly had a software program vulnerability and though a software program patch was printed in 2010 and 2013 the info controller didn’t replace software program each the occasions as a result of lack of formal course of to Assessment and apply software program updates. The failure to replace the database software program and the safety flaws within the IT safety system made the corporate very weak to a cyber-attack.
The safety flaws within the firm’s JBoss Software net server have been exploited between 14th and 28th October 2013. The attacker used the vulnerability within the utility server to inject a malicious JavaScript code referred to as “JSPSpy” on the agency’s web site. JSPSpy enabled the attackers to remotely view and modify the supply code of the web site and question the database containing the small print of the shoppers. It additionally let the attackers open a command shell permitting them to remotely execute privileged working system instructions. The attackers particularly focused and downloaded the fee card particulars. Although the cardboard numbers have been encrypted the attackers have been in a position to establish the keys used within the encryption and therefore might decrypt the cardboard numbers. On the time of the assault the database contained a complete of 110,096 dwell card particulars, which have been at a threat of being accessed and utilized in fraudulent transactions. The agency grew to become conscious of the assault on 14th November 2013 and instantly employed unbiased forensic knowledge specialists and wrote to 93,389 affected clients, to make them conscious of the assault. The corporate additionally supplied the affected clients free entry to Information Patrol, which is an id fraud monitoring service.
After the assault Staysure was fined with an quantity of £175,00 by the ICO for the reason that firm didn’t comply to the Cost Card Business Information Safety Commonplace (PCI DSS) , which is an ordinary administered by PCI Safety Requirements Council (PCI SSC) to extend fee card safety and lower the transaction frauds over the web.
References:
http://securityaffairs.co/wordpress/21002/cyber-crime/staysure-hacked.html
http://www.theinquirer.net/inquirer/news/2321017/staysure-travel-insurer-admits-to-credit-card-theft
http://trainsure.com/news-posts/insurance-times-reports-another-cyber-attack/
http://www.moneywise.co.uk/news/2014-01-06/staysure-insurance-customer-data-stolen-hackers
Threat Analysis and Risk assessment
The aim of risk Assessment and threat assessment is to maximise the safety of the three important pillars of safety particularly confidentiality, Integrity and Accessibility whereas nonetheless offering usability and performance. A Risk to any group or a person is an interactive relationship of risk, asset and vulnerability. The varied ranges of threat will be represented because the product of the impression and likelihood (probability).
|
Quantitative Measure |
Qualitattive Measure |
Description |
|
5 |
Excessive |
A excessive degree threat can happen continuously and can have a drastic impact on the group. Sever measures will likely be wanted in an effort to mitigate a excessive degree threat. |
|
four |
Medium Excessive |
A medium excessive threat can happen/recur with excessive likelihood however won’t persist. If it happens the group can have a big or sever impact. |
|
three |
Medium |
A medium degree threat is prone to occur beneath many circumstances and if a medium degree assault happens it could actually have reasonable to extreme results on the group. |
|
2 |
Low Medium |
A low medium threat will be thought of when the group can have a minor or reasonable impression on account of an assault. A low medium threat can happen often or won’t happen in any respect and will be mitigated simply. |
|
1 |
Low |
The chance is taken into account to be low when the probability of an assault on an entity is low and the impression of the assault on the entity is negligible or minor. Low dangers won’t ever or hardly ever occur and will be mitigated simply. |
Desk 1: Risk Score Scale
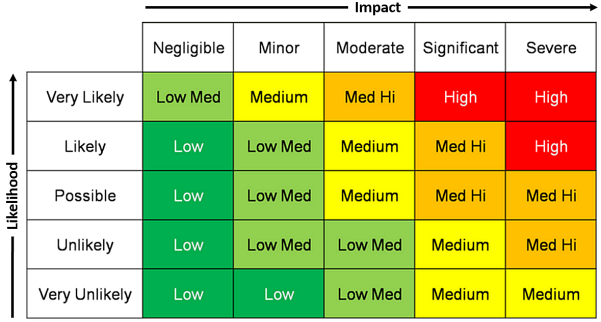
Figure1.
Determine 1 exhibits a threat matrix which represents the assorted ranges of threat. A vulnerability is a weak spot within the system that may be exploited by an attacker or will be unintentionally triggered by an individual throughout the group. The chances are the likelihood that any vulnerability will likely be taken benefit of or the vulnerability will likely be triggered by somebody unintentionally. The chances are associated to attacker’s intent, attacker’s potential and attacker’s goal. If a sure vulnerability is exploited the impression on a corporation will be expressed in phrases like Negligible, Minor, Reasonable, Vital, Extreme.
The desk beneath exhibits a threat assessment structure for Staysure.co.uk. The Agency had a number of safety flaws within the system, which the attackers exploited to achieve entry to buyer info.
|
Asset |
Threat |
Vulnerability |
Threat Actor |
Threat vector |
Penalties |
Likeli hood |
Affect |
Risk |
|
Buyer Private particulars |
Will be assessed and manipulated |
The database had no safety process in place therefore the info was extremely accessible. |
Hackers or an individual throughout the group (insider). |
Getting access to the database by gaining access to the webserver or SQL injections. |
Personal particulars of the staff like title, deal with, cellphone will be accessed and used and even modified. |
Potential (three/5) |
Vital (four/5) |
Medium Excessive |
|
Firm web site |
Supply code of the web site will be modified and malicious code will be injected and made to run on the browser (Cross website scripting). |
Cross website scripting will be carried out on the web site if safety measures should not taken care of whereas creating the web site. |
Hackers or an insider. |
Net pages |
Malicious code will be injected into the net pages thus permitting entry to the net server and the database. |
Very Probably (5/5) |
Extreme    (5/5) |
Excessive |
|
Information controllers system |
No intrusion detection system. |
A system with no correct safety measures will be simply penetrated. |
Hackers or an insider making an attempt to get unauthorized entry. |
Backdoor created within the net server. |
Having access to the info controllers system permits the risk actor to execute Privileged working system instructions |
Very doubtless (5/5) |
Extreme (5/5) |
Excessive |
|
Monetary card particulars |
Storing monetary knowledge incorrectly. |
Unencrypted card particulars saved within the database |
Hackers or an insider making an attempt to get unauthorized entry. |
Website online supply code can be utilized to question the database |
Card particulars can be utilized to make fraudulent transaction and cloning. |
Very doubtless (5/5) |
Extreme (5/5) |
Excessive |
|
Encryption key |
Encryption algorithms can be utilized to calculate the encryption key |
Easy encryption algorithm used to kind an encryption key. |
Hackers or an insider. |
Reverse engineering. |
If the encryption secret is compromised all of the encrypted knowledge will be decrypted. |
Potential (three/5) |
Extreme (5/5) |
Medium Excessive |
|
CVV quantity |
Storing CVV numbers within the database is a excessive threat. |
CVV numbers if not encrypted will be simply learn if the attacker will get entry to the database. |
Hackers or an insider. |
Website online supply code can be utilized to question the database for CVV numbers. |
CVV numbers can be utilized to show authentication whereas doing on-line transactions. |
Very doubtless (5/5) |
Extreme (5/5) |
Excessive |
|
JBoss Software Server |
Unpatched and outdated software program’s and no intrusion detection system |
Scripts will be uploaded to the server which when executed provides distant administration entry to the server. |
Hackers or an unauthorised insider. |
Backdoor’s created on the server by way of malicious script. |
As soon as administration entry is acquired on the server varied admin actions will be initiated and the hosted net servers will be accessed. |
Probably (four/5) |
Extreme (5/5) |
Excessive |
|
Database |
Database injections and unmanaged knowledge |
The information within the database can extremely weak to SQL injections and will be extremely inconsistent. |
Hackers |
SQL injections |
Information will be erased and stolen from the database and utilized in a fraudulent method. |
Probably (four/5) |
Extreme (5/5) |
Excessive |
https://www.towergateinsurance.co.uk/liability-insurance/smes-and-cyber-attacks — take away later
http://resources.infosecinstitute.com/how-to-prevent-cross-site-scripting-attacks/ –take away later
Safety Structure
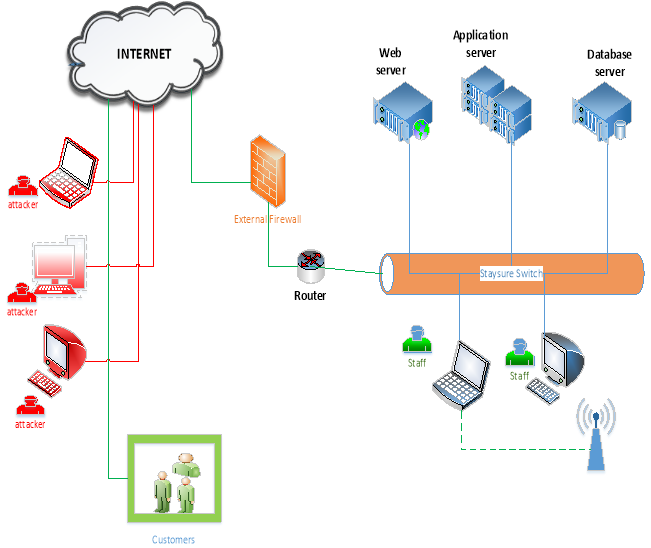
Determine: 2
Determine 2 exhibits safety structure for Staysure throughout the time of the assault
Safety Suggestions
Staysure.co.uk had no safety insurance policies in place which will be sited as the bottom for the cyber-attack. Being an insurance coverage firm and holding private data of hundreds of thousands of consumers the corporate ought to have had safety procedures in place. It can be crucial that the staff of an organization are skilled and made conscious of the significance of data knowledge safety. The truth that the attackers took benefit of the software program vulnerability within the JBoss utility server though there have been patches out there to repair the vulnerabilities exhibits the ignorance of the info controller in the direction of info safety. Desk 2 lists safety suggestions which might have prevented the assault.
|
Safety Suggestions |
Descriptions |
|
Safety insurance policies |
Safety insurance policies is an integral a part of any group. Staysure being an insurance coverage firm and dealing with hundreds of thousands of buyer data ought to have had strict firm safety insurance policies which might have prevented the assault. |
|
Safety coaching and consciousness |
The workers of Staysure have been clearly not conscious of the significance of information safety and administration. The workers ought to have been offered good knowledge safety and knowledge administration coaching and made conscious of data safety. |
|
Cost Card Business Information Safety Commonplace (PCI DSS) – add appendix |
When a corporation handles private data of consumers it’s vital that the group follows sure business requirements for knowledge storage. In keeping with PCI DSS the CVV numbers mustn’t have been saved within the database. If the requirements have been adopted the assault wouldn’t have a significant impression. |
|
Information storage and knowledge safety |
Information storage has each bodily and logical safety features. The logical side being knowledge authorization, authentication and encryption. The bodily features embrace the place by which the servers are positioned, it ought to be protected from heat-waves, energy fluctuations and different bodily parts. In case of Staysure the fee card particulars and the CVV numbers ought to have been encrypted with a powerful encryption algorithm from the very starting and the database server ought to have had an intrusion detection and prevention system which might have prevented entry to the database. |
|
Patch administration |
Unpatched techniques and software program’s pose an enormous risk to a corporation. Essentially the most environment friendly technique to protect from assaults is to have patch administration process to make it possible for all of the techniques and software program’s are patched on common foundation. If Staysure had patched the vulnerabilities within the Jboss utility server and software program, the attackers wouldn’t have been in a position to exploit the vulnerability. |
|
DMZ (Demilitarized Zone) |
The servers which are confronted in the direction of the general public ought to be stored within the DMZ, in order that they are often separated from the personal community. If a malicious celebration positive aspects entry to the server, he will likely be remoted within the DMZ and won’t be able to assault the personal community. If Staysure had a DMZ the attackers wouldn’t be capable of entry knowledge on the personal community. |
|
Encryption |
Encrypting any worthwhile info of consumers is important in an effort to defend buyer knowledge from being accessible and utilizing a powerful encryption secret is important to serve the aim of encryption. The information controller ought to have had made positive to encrypt the CVV and the cardboard quantity and ought to have used a powerful encryption key. |
|
IDS |
Staysure ought to have had Intrusion detection systems in order that the intrusion by the attacker might have been detected and would alert the authorities thus stopping excessive impression |
|
Firewalls |
|
|
Prevention of human errors |
http://www.ibm.com/support/knowledgecenter/SSTFWG_4.3.1/com.ibm.tivoli.itcm.doc/CMPMmst20.htm — patch administration coverage.
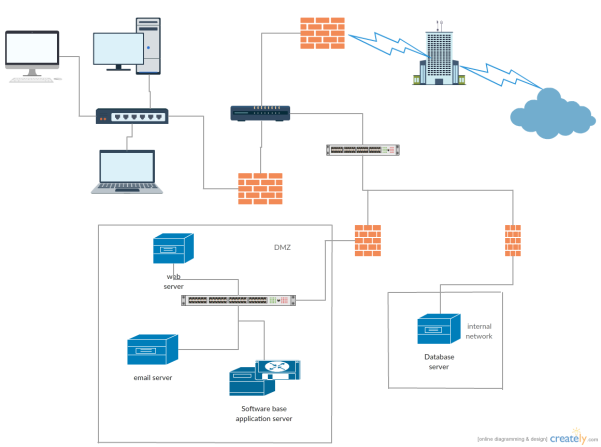
Excessive degree safety diagram to forestall assaults
Every Student Wants Quality and That’s What We Deliver
Only the most qualified writers are selected to be a part of our research and editorial team, with each possessing specialized knowledge in specific subjects and a background in academic writing.
Our prices strike the perfect balance between affordability and quality. We offer student-friendly rates that are competitive within the industry, without compromising on our high writing service standards.
No AI/chatgpt use. We write all our papers from scratch thus 0% similarity index. We scan every final draft before submitting it to a customer.
When you decide to place an order with Nursing Study Bay, here is what happens:
Find an expert by filling an order form for your nursing paper. We write AI-plagiarism free essays and case study analysis. Anytime!