Graduate Essay Writers
Only the most qualified writers are selected to be a part of our research and editorial team, with each possessing specialized knowledge in specific subjects and a background in academic writing.
To hire a writer, fill the order form with details from your nursing assessment task brief—assignment instructions.
Posted: April 24th, 2023
Study Bay Coursework Assignment Writing Help
Jasjeet Singh
What are the steps project managers must incorporate to uphold the security, privacy and disaster recovery policies to prevent Companies sensitive and vital corporate Data?
Abstract– Security, disasters and privacy are risks to a project and to a project manager. But project managers are trained to deal with risks. These risks are best addressed when the project manager fully understands them. In a nutshell, we can say it’s all about protection of vital data and its critical element CIA(confidentiality, integrity, and availability) including the machines and process that use, store, and transmit that data. Security is a risk to project managers for both implementing a project and perhaps the project itself if it is IT or telecom related. In this paper, I will include the data security risks facing a project manager, How to protect the CIA Triad using various security policies, standards, and procedures. And I will try to touch some more information security related aspects like Security Awareness and privacy protection, etc.
Keywords-Project management; Project Manager; Data Security; Privacy; Security Policies; Confidentiality; Security Awareness.
Almost every project generate or use, some form of information and information technology. Mostly, this information needs to be preserved or isolated by some form of security. Security planning and implementation is an integral part of the overall project life cycle which also include many different issues to be considered when planning a project. Whereas finally what is being safeguarded is the data produced by the machines, the information that data is used to create, and in some manner, the conclusions made based upon that vital data.
A security threat is something that jeopardizes any of the CIA Triad (availability, confidentiality, and integrity) of a machine’s data. Security flaws and risks emerge from such threats. Solutions and planning to manage such items begins in the very initiation stages of a project’s life with the identification of any of these security related flaws, risks, and threats. In parallel with each phase, efforts work towards constantly identifying new threats and reducing the identified security risks through the diligent planning and proper implementation of risk mitigation strategies specifically developed to resolve each unique threat specifically. Security of vital data and associated technology systems must be considered when planning projects, developing applications, implementing systems, or framework etc. So as to be effective and efficient, security must be organized for and embedded into the systems from the very starting, and monitored periodically throughout the life of the project, and be maintained all along the life of the system. Thereby the result is planning as soon as possible in early stages and embedding security into all phases of a project’s life cycle is usually considerably easier and much less cost consuming than waiting till the later project phases to consider it. On the moment when addressing the security for the majority of the data frameworks, it might be a chance to be decayed under three principal segments that are; communications, hardware, and software. Arranging how every from claiming these zones may be ensured includes not the main attention by the people, policy, practice etc. and also, financial considerations with furnish for those Audit from claiming the framework, asset procurement, execution of security solutions, progressing security maintenance and so on.
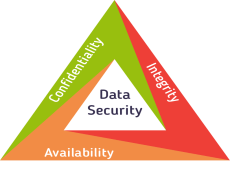
The image shows the main goal of such efforts which are to maintain the availability, confidentiality, and integrity of vital information. All information system must maintain:
An ordinary Project Management technique doesn’t incorporate subtle elements regarding guaranteeing integrity, confidentiality, Furthermore availability for the majority of the data or those protections about particular data.
Background need to be demonstrated that mostly the information security or privacy experts would not consult regarding the undertaking until those test phase, alternately much more terrible The point when the project needs with be marked off or executed Also about to go live. These conditions will feel thick, as commonplace on the majority of the data security experts Also privacy officers indistinguishable. This cautiously might prompt postponements previously, sign-off What’s more go-live alternately significantly more repulsive another information skeleton being moved under preparing without expanding security Also security controls completed. This means exploitation of risks such as:
Moreover “bolting on” security instruments & controls alternately privacy controls toward those end of the development, for example, another provision or the usage of a new data framework is really unreasonable Furthermore drawn out. Data information and framework security What’s more security methods oughta chance to be inserted under the organization’s venture administration procedure. This ensures that majority of the data security Also security dangers would identify, assessed, figured out how What’s more tended to ask and only an undertaking. This approach Might make associated for during whatever endeavor regardless to its character, e.g. an endeavor for focus profits of those business process, IT, office organization Moreover different supporting manifestations. Venture supervisors would continuously set under a considerable measure from claiming weight to guarantee they convey on time What’s more inside plan. On accomplish execution of a secure Also industry consistent legitimate & administrative necessities data system, it may be vital to take part for the majority of the data security and security topic masters from those minute a feasible ticket may be recognized to Creating. The two main approaches to project management are:
Both methodologies need pros Furthermore cons Furthermore, we won’t talk about whatever points of these two approaches, rather it takes a gander during the place what’s more entryway data security Also privacy ought to a chance to be joined under those project management cycle, in any case about which methodology is picked.
Everyone dares organization methodologies to take after a tantamount high-cap convert starting with asserting 4 alternately 5 steps, in the passages underneath those steps to that Agile technique would previously, (brackets). Every for these steps needs their goal/objective, in addition, an arranged starting with guaranteeing deliverables to that step. For every to these steps, those one assignment director ought to should incorporate a security proficient. Incorporating security under exercises beginning with that start will Abstain starting with each moment abstain? In addition (often very) irrationally additions later on in the project. The individuals taking then afterward slug concentrates give to an Audit of the lion’s share of the information security Also privacy-related considerations for each phase. More details on this topic can be studied on the internet.
The waterfall project management techniques discuss that for managing Also controlling the one project phases, An amount from claiming checkpoints, turning points or gateways ought further bolstering be presented.
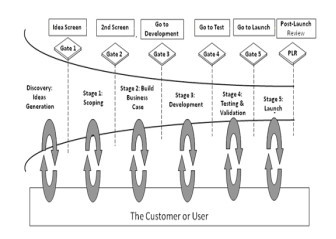
The main motive of these gateways is to make sure that all criteria or needs are fulfilled or not, all required deliverables for that phase are done or not, and to review if the project is still “on time/within budget”. These gateways are the instances in time during a project where security and compliance milestones can be introduced to safeguard that the project in compliance with all agreed business needs, including security and privacy formulations. Underneath are some checks, decisions, and lists that should be implemented from an information security and privacy point of view:
The job of Information Security is primarily to ensure CIA in place but there is a common misconception that only IT is responsible for it. But they’re not!! Then who is responsible for Information Security in your organization or say for the project you’re managing?
Let’s think of below:
PM is the one who:
So need to include Information Security within the project process right from the Initiation. We can fit it in when developing Project Charter
Project Plan – integrate information security
Scope Management
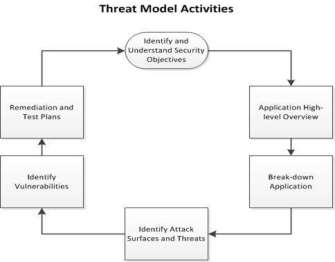 Figure 3: Threat Activity model
Figure 3: Threat Activity model
Procurement
Quality
Next, integrate within your Project Plan.
Cost & Time
Stakeholder Management
Project Risk Management – Information Risk Assessment
Let’s review the basics once again:
Define Information Risk  Risk is a factor of the likelihood of a given threat sources exploiting a particular potential vulnerability and the resulting effect of that adverse event on the organization.
Qualitative Risk Assessment
Quantitative Risk Assessment
Risk Response
Note: SIME: Security Information and Event Management  DLP: Data Leakage Protection  DRM: Digital Rights Management.
HR/People – Manage Security with People
Security Skills Assessment
Security Awareness

Figure 4: Security Awareness Training
Project Communication – Secure what you communicate
Comply with the security policies
Checkpoint for data transfers and storage
Establish administrative controls
Project Execution – Implement effective control
Direct and Manage Project Work
Manage Communication

Figure 5: Communication Management
Monitor & Control – Pro-active check and act
Control Scope & Risks
Security Incident Management
Manage 3rd Party Risk
Project Closure -Secure disposal
Formal Sign Off
Operational Handover
Data Disposal
Information Security plays a very important role in the development of every project irrespective of projects magnitude. So the project manager has to be very much alert and attentive to check and to meet the protocols so as to preserve the vital corporate data of the organizations during each phase of the project development.

Figure 6: Template for Questionnaire to review security of project
The project manager must use various new techniques to embed the security into the project from the very initiation phase one of such technique is to use Questionnaire to review the security of the project.
Project Managers can also look for a new secured Software development life cycle model which incorporates all major aspects of the data security, privacy, and recovery for a software development.
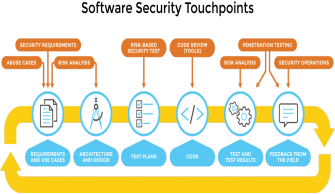
Those A large cost savvy approach to managing security under products or techniques is to actualize all the security Furthermore privacy controls and mechanisms under the configuration, Including them later alternately. After the project needs to be run live, will be significantly a greater amount exorbitant and might diminish those Return-on-Investment of the project altogether.
|
[1] |
“Security Issues that Project Managers at CDC Need to Address,” CDC Unified Process Project Management, vol. 2, no. 6, June 2008. |
|
[2] |
M. Dean, “A riskbased approach to planning and implementing an information security program,” in PMI, 2008. |
|
[3] |
B. Egeland, “Learn 3 Ways to Ensure Your Project Data is Secure.,” Is Project Security that Important?, July 2, 2015. |
|
[4] |
R. J. Ellison, “Security and Project Management,” Security and Project Management | USCERT, February 06, 2006. |
|
[5] |
D. E. Essex, “government database project outsourcing,” A matter of public record, August 2003. |
|
[6] |
S. Fister Gale, “Safeguarding the data treasure,” February 2011. |
|
[7] |
S. Hendershot, “Security guards datasecurity initiatives for Project Managers,” in Cost Control (https://monkessays.com/write-my-essay/pmi.org/learning/library?topics=Cost+Control), Sustainability (https://monkessays.com/write-my-essay/pmi.org/learning/library?topics=Sustainability), September 2014. |
|
[8] |
C. Klingler, “Security, privacy and disaster recovery for the project manager,” in Cost Control (https://monkessays.com/write-my-essay/pmi.org/learning/library?topics=Cost+Control) , Sustainability (https://monkessays.com/write-my-essay/pmi.org/learning/library?topics=Sustainability), 2002. |
|
[9] |
Monique, “Information Security & Privacy as part of Project Management,” 18 March, 2015. |
|
[10] |
M. Pruitt, “Security Best Practices for IT Project Managers,” SANS Institute, June 18, 2013. |
Table of Figures
Figure 1: CIA Triad: https://www.checkmarx.com/wp-content/uploads/2016/06/Data-Securi
Every Student Wants Quality and That’s What We Deliver
Only the most qualified writers are selected to be a part of our research and editorial team, with each possessing specialized knowledge in specific subjects and a background in academic writing.
Our prices strike the perfect balance between affordability and quality. We offer student-friendly rates that are competitive within the industry, without compromising on our high writing service standards.
No AI/chatgpt use. We write all our papers from scratch thus 0% similarity index. We scan every final draft before submitting it to a customer.
When you decide to place an order with Nursing Study Bay, here is what happens:
Find an expert by filling an order form for your nursing paper. We write AI-plagiarism free essays and case study analysis. Anytime!